Stopping Data Breaches: Whose Responsibility Is It?
— May 26, 2015
Data breaches remain a persistent and costly issue for businesses, with the Verizon 2015 Data Breach Investigations Report revealing 2,122 confirmed breaches in 2014, resulting in losses of $400 million. Despite such reports, many breaches are only uncovered much later. For instance, CareFirst BlueCross BlueShield discovered in May 2015 that a breach from June 2014 had exposed the names, birthdates, and email addresses of 1.1 million members. The delay in detection illustrates a critical issue: gaps in proactive security measures and oversight.
Other incidents from the same period further underscore this concern. The Federal Reserve Bank of St. Louis revealed that hackers redirected traffic from its research website, potentially exposing users to phishing attacks and malware. Similarly, Australian telecom giant Telstra discovered unauthorized access to the network of its subsidiary, Pacnet, only after finalizing its acquisition. These examples show that data breaches are neither confined to specific industries nor limited to direct financial loss; they erode customer trust and tarnish reputations.
To address these challenges effectively, organizations must recognize that stopping cybercrime requires collaboration, both within and outside the company. This includes active participation from internal teams, external partners, and even customers.
Internal Collaboration: A Shared Responsibility
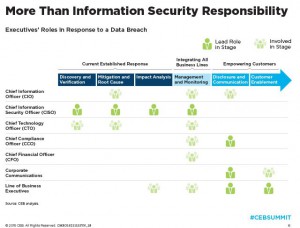
Jason Malo, a Research Director at CEB TowerGroup, emphasized during the 2015 CEB Financial Services Technology Summit that security cannot be relegated solely to the Chief Information Security Officer (CISO). While the CISO is a key figure in managing and monitoring security efforts, combating data breaches effectively demands a coordinated approach involving multiple teams.
The Chief Information Officer (CIO) and Chief Technology Officer (CTO) must work closely with the CISO to provide technical expertise in breach detection and mitigation. Meanwhile, compliance officers, communication teams, and business line executives play essential roles during the disclosure phase. They ensure accurate reporting, mitigate legal exposure, and rebuild customer trust.
Such collaboration is not just about assigning roles; it involves establishing clear communication channels and fostering a culture of shared accountability. A cohesive internal response reduces reaction time, minimizes damage, and enhances customer confidence.
Empowering Customers: A Critical Element
While internal collaboration is essential, customer engagement is equally important in addressing and preventing data breaches. Malo argues against the prevailing notion of a “frictionless” customer experience in fraud prevention, where customers are largely passive participants. Instead, he advocates empowering customers by involving them in the security process.
Providing customers with clear, actionable guidance after a breach is critical. A breach response must be honest, prompt, and compassionate. Businesses should prioritize answering the question, “What should I do now?” with tailored solutions that cater to different risk profiles. For instance, offering credit monitoring, encouraging regular password updates, or providing multi-factor authentication options can help customers secure their data.
An Associated Press–GfK poll highlights the gap between consumer awareness and action. While 41% of respondents checked their credit reports after a breach, only 31% updated passwords, and just 18% signed up for credit monitoring. This demonstrates that customers often lack the tools or knowledge to take appropriate measures. By investing in customer education, companies can help individuals take proactive steps to protect themselves.
Building a Stronger Security Culture
Investing in customer empowerment and internal collaboration lays the groundwork for a resilient security culture. Companies must recognize that data breaches are not one-off events but ongoing threats that require continuous vigilance.
For instance, educating customers about security best practices even before a breach occurs can be an effective preventive measure. Customers who are aware of how to safeguard their data are less likely to fall victim to phishing schemes or other forms of exploitation. This not only reduces the immediate impact of a breach but also strengthens the company’s reputation for prioritizing customer safety.
Similarly, businesses can benefit from regularly updating and testing their internal protocols. Collaborative exercises, such as simulated breach scenarios, can prepare teams for real-world incidents. These simulations help identify weaknesses in current processes and ensure that all stakeholders are aligned in their response strategies.
The Economic Impact of Data Breaches
The financial stakes of data breaches continue to rise. A Ponemon Institute survey found that 83% of financial services companies and 44% of retail firms experienced over 50 attacks per month. Juniper Research projected that the global cost of malicious data breaches would exceed $2 trillion by 2019, with the United States accounting for over 80% of the losses. For context, this amounts to 7.6% of the U.S. GDP in that year.
Such figures highlight the need for businesses to treat cybersecurity as a core operational priority. Beyond direct financial losses, the long-term effects of breaches—such as diminished customer trust, legal penalties, and reputational harm—can have far-reaching consequences.
External Collaboration: Partnering for Security
In addition to internal efforts, businesses should seek external partnerships to enhance their cybersecurity measures. Outsourcing to trusted technology providers, such as Vietnam-based S3Corp, can offer specialized expertise in web and mobile security. These partnerships can help companies identify vulnerabilities, implement robust defenses, and stay updated on emerging threats.
Working with external experts also enables businesses to leverage advanced technologies that may be cost-prohibitive to develop in-house. For example, machine learning algorithms can detect unusual activity patterns, while blockchain technology can secure sensitive transactions. By integrating these solutions, companies can create a multi-layered defense system that adapts to evolving threats.
Moving Forward
Stopping data breaches requires a holistic approach that combines internal coordination, customer engagement, and external collaboration. Each component plays a crucial role in building a secure environment that protects both company assets and customer data.
As cyber threats grow in scale and sophistication, businesses must adopt proactive measures rather than reactive ones. This includes fostering a culture of shared responsibility, investing in education and technology, and forming strategic partnerships with specialized providers. By doing so, companies can minimize the risk of breaches, reduce their impact, and maintain the trust of their customers.
Through consistent efforts and collaboration, businesses can not only safeguard their operations but also contribute to a broader ecosystem of cybersecurity awareness and resilience.